Today, encrypting data at rest is crucial for enhancing security of our applications. Besides, it might be a requirement for your compliance regulations. Whatever the reason is, it is a best practice to encrypt your Amazon Elastic Block Storage (EBS) volumes. In this post, I will show you how to encrypt an Amazon EBS volume using its integration with Amazon Key Management Service (KMS).
What is Amazon KMS?
Amazon EBS is integrated with Amazon KMS to provide encryption. Without KMS, you would need a key management infrastructure to keep your encryption keys safe and use them efficiently. Amazon KMS provides these features out of the box as a managed service.
On Amazon KMS, the encryption keys or called Customer Master Keys (CMKs) and there are three types of CMKs:
Customer Managed CMKs: These are CMKs that you created directly using Amazon KMS. You own, manage them and have full control. These keys can incur monthly costs when usage exceeds free tier and they are subject to account limits.
AWS managed CMKs: These are CMKs created by AWS services integrated with KMS on your behalf and we will use one of them in this post. You can view these keys, but you cannot manage them. The AWS service created it handles the management. These keys do not have monthly fees, but they can have usage fees according to AWS services that make use of them. They are not counted againts your limit for KMS keys in the region as well.
AWS owned CMKS: These CMKs are owned and managed by AWS. They can be used by AWS services to protect your data and they are not subject to KMS costs or limits.
Amazon EBS creates an AWS-managed CMK automatically when you encrypt a volume. You can use this CMK or create a customer-managed CMK to use in the encryption process. Now, let’s continue with EBS encryption.
Amazon EBS Encryption Concepts
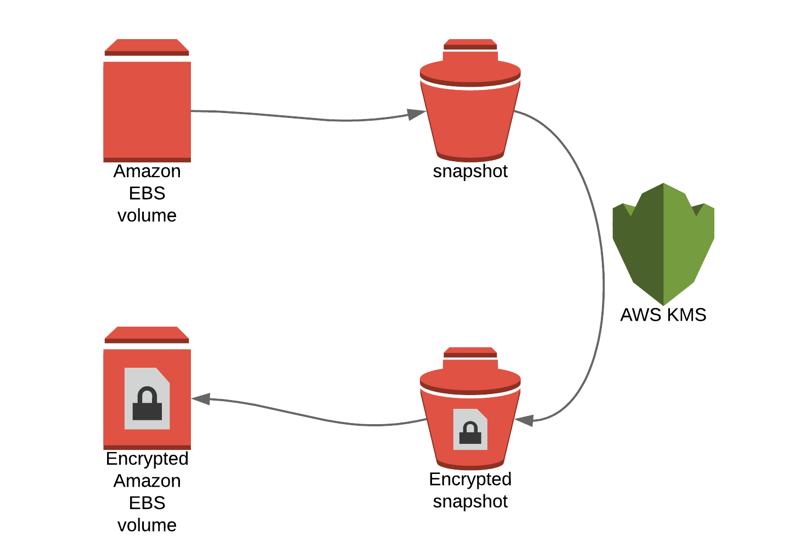
When you encrypt an EBS volume, all these resources are encrypted as well:
As you would expect, data at rest inside the volume is encrypted.
When you attach this EBS volume to an EC2 instance, all communication between that instance and EBS volume is encrypted.
When you create a snapshot from an EBS volume, the snapshot is also encrypted.
When you create a volume from an encrypted snapshot, the new volume is also encrypted.
All current EBS types supports encryption. But, only certain EC2 instance types support encrypted EBS volumes. However, I can say that the most of the latest instance types support them such as t2, m4, m5, etc.
Creating Encrypted EBS Volumes
There are two ways of creating an encrypted EBS volume: Either you will enable encryption when creating it or you will create it from an encrypted snapshot.
Creating an encrypted EBS volume from scratch
You can choose to encrypt an EBS volume during EBS volume creation on Amazon EC2 Management Console. As you can see below, there is an option for encryption as below.
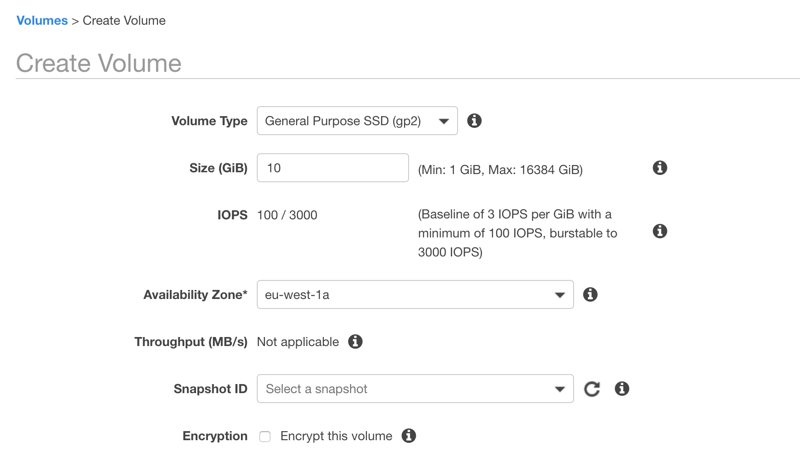
When you select Encrypt this volume option, a select box appears which displays CMKs available that can be used in this encryption. As you can see, Amazon EBS has created one for me as an AWS-managed CMK.
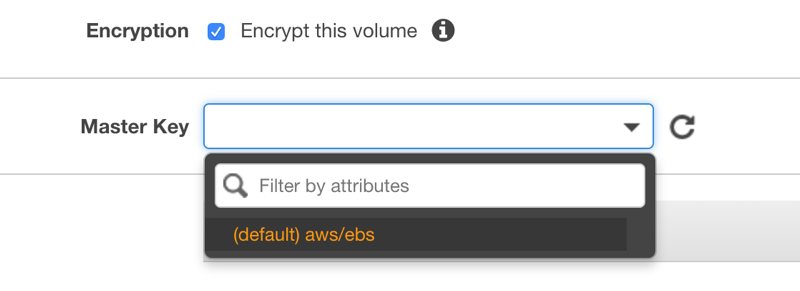
After you select the key, the details about it displayed below the selection.
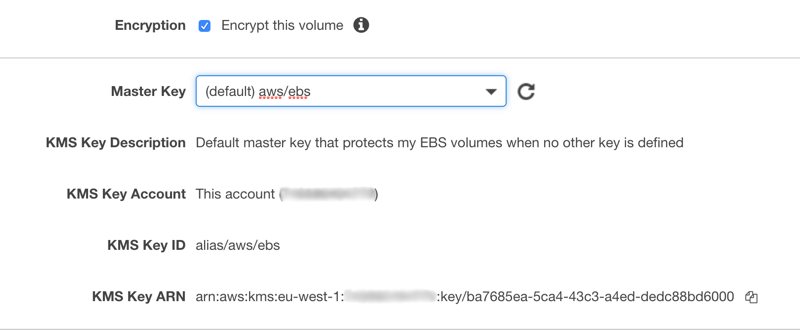
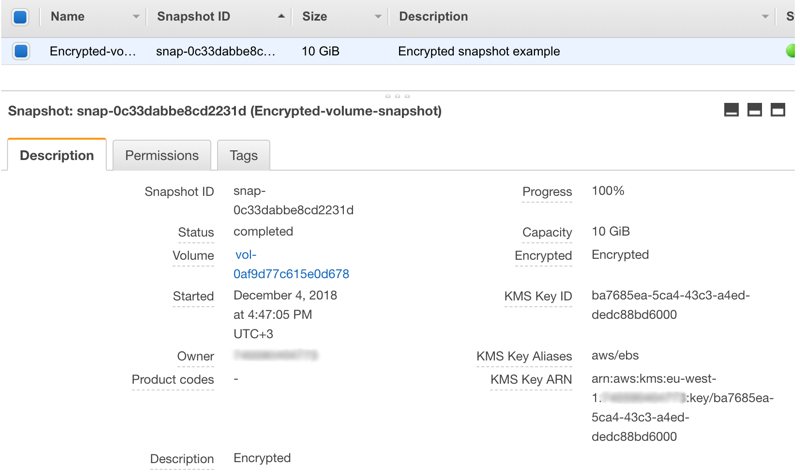
After creating the volume you can access encryption information from the description panel. As you can see below, KMS Key ID, aliases (which would be also aws/ebs if you select AWS-managed key) and its Key ARN.
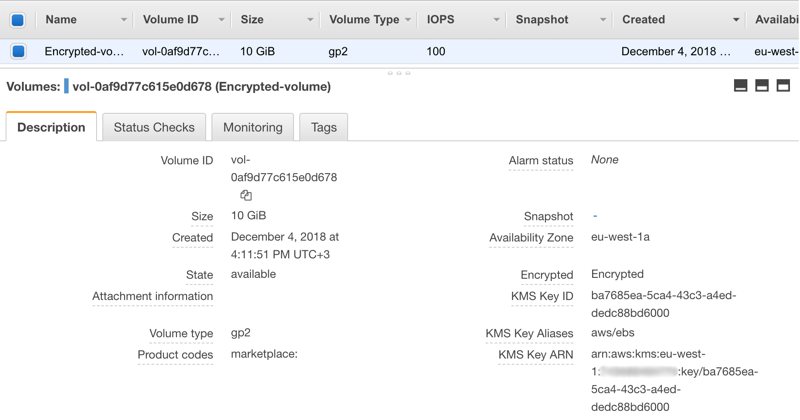
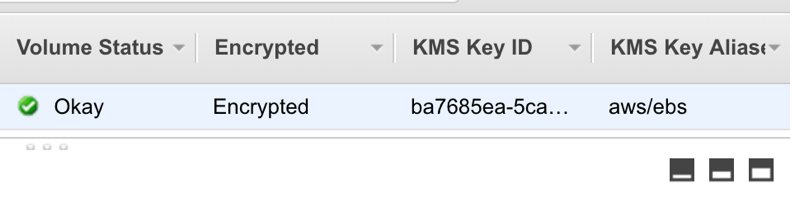
You can also view the encryption information on the list if you scroll right.
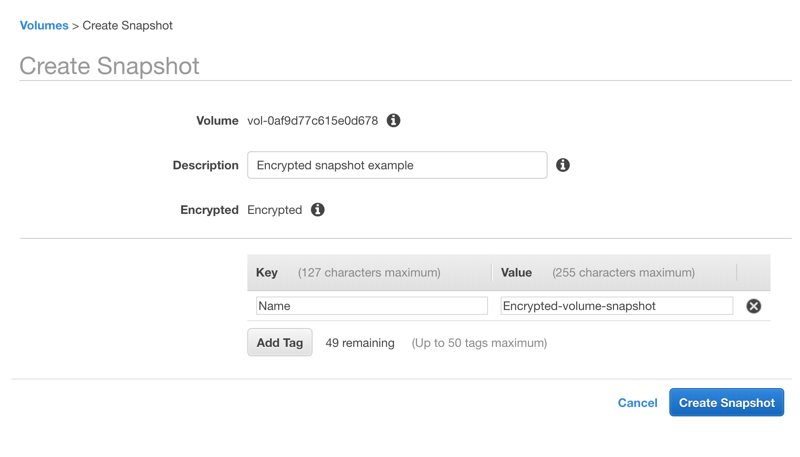
Creating snapshots from an encrypted EBS volume
When you create a snapshot from an encrypted EBS volume, it is automatically encrypted. On snapshot creation, you can display this information as below.
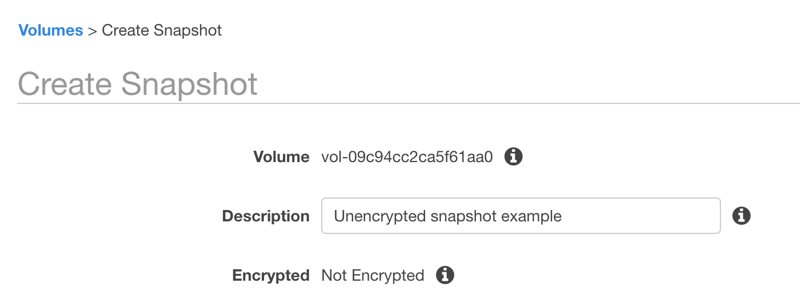
However,if you create a snapshot from an unencrypted volume, this time encryption information is Not encrypted.
After creating an encrypted snapshot, you can view the encryption details from the description panel similar to the EBS volume it was created from.
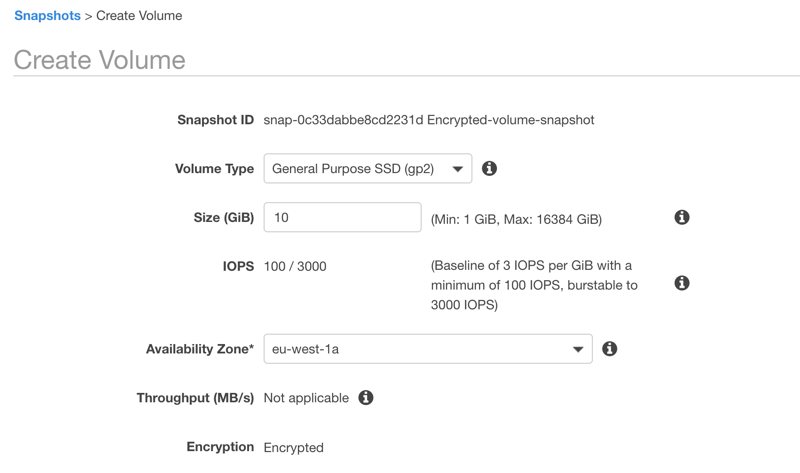
Creating an encrypted EBS volume from an encrypted EBS snapshot
It is simple to create an encrypted snapshot from an encrypted EBS volume. In contrast to creating an EBS volume from scratch, this time nor you can select whether it will be encrypted not you can change the encryption key. It gets the encryption details from the snapshot. As you can see, you cannot create an unencrypted volume from an encrypted snapshot.
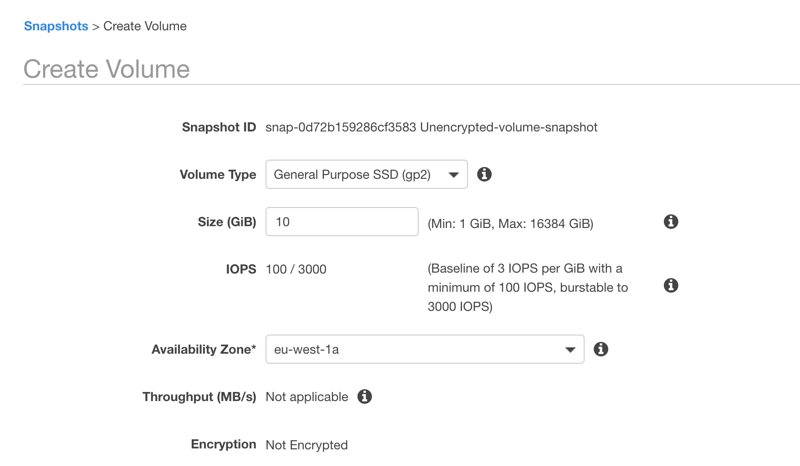
Similarly, you cannot create an encrypted volume from an unencrypted EBS snapshot directly. As you can see below, it is decided as Not encrypted when you try to do so.
Creating an encrypted EBS volume from an unencrypted one
You cannot encrypt an unencrypted volume after creating it. However, you can create a new encrypted one from it. There is no direct way to achieve this. You need to create a snapshot which will be unencrypted as we discussed above and create an encrypted snapshot from this unencrypted snapshot by copying it.
When you try to copy an unencrypted snapshot, you will see an encryption option as below.
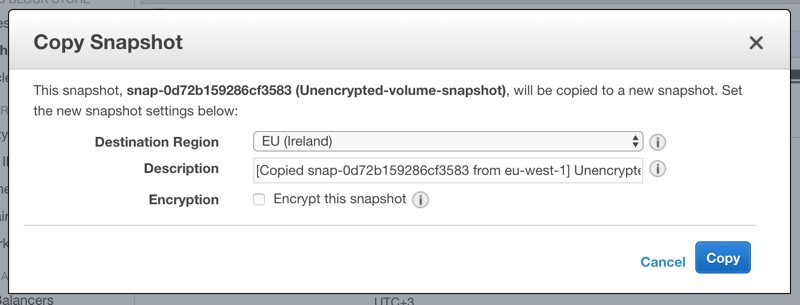
Similar to creating a new EBS volume, when you select Encrypt this snapshot, a list for existing CMKs will be displayed.
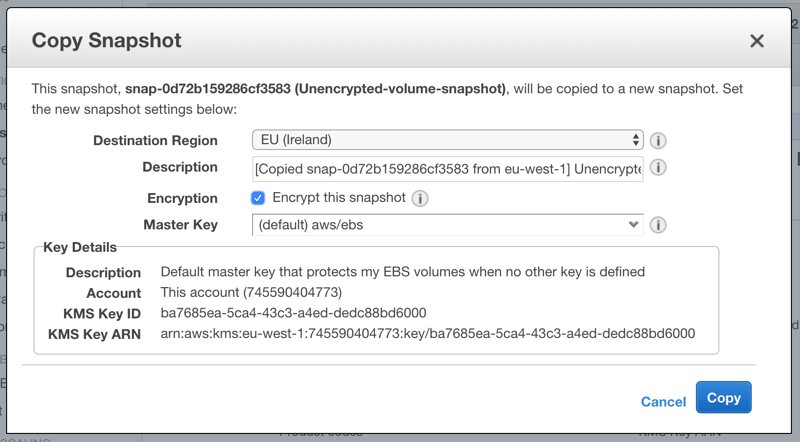
After creating your encrypted snapshot, you can use it to create an encrypted EBS volume using the same steps we discussed earlier.
How about creating an unencrypted volume from an encrypted one?
You cannot remove encryption from an encrypted snapshot by copying it and you cannot create an unencrypted volume from an encrypted one. The only way is mounting both encrypted and unencrypted volumes on an EC2 instance and copying the data between them using tools like rsync.
Conclusion
Encrypting data at rest is simple on AWS when using Amazon EBS volumes and it is a best practice. There is practically no downside in terms of performance and it will obviously enhance your applications’ security even if you use them only in private subnets. Hence, it is time to start encrypting your volumes if you have not done this yet.
Creating an encrypted AMI is mostly similar to enabling encryption on EBS volumes. However, we can also take a look at it in the following blog posts.
Thanks for reading!