AWS CloudFormation Stack Policy Conditions: Don't Replace or Delete My DB Instances on Stack Updates
- by Emre Yilmaz
- Apr 18, 2022
- AWS • DevOps • AWS CloudFormation • Amazon RDS
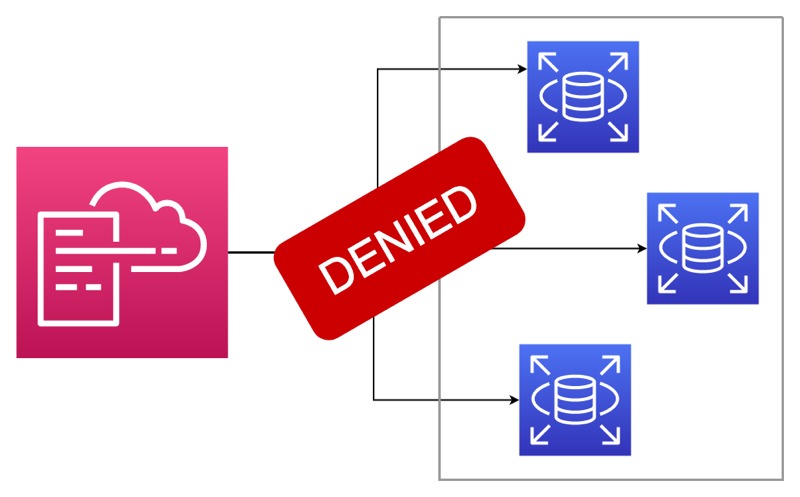
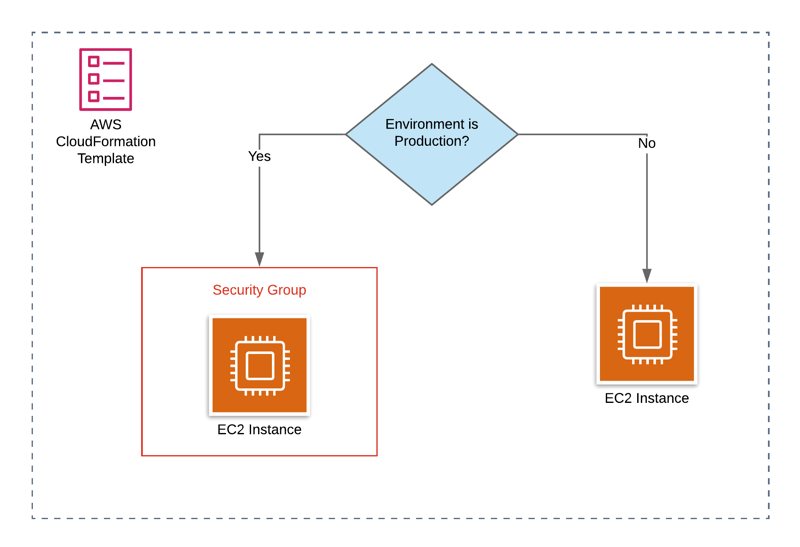
Stack policies are among the most helpful features of AWS CloudFormation for protecting your stacks from unintended updates. Let’s say that you have an Amazon RDS instance that you manage with AWS CloudFormation. After a while, you change one of its attributes and update your stack. Guess what! The update you considered innocent was not so after all. It replaces your database instance with all the data inside. It’s a nightmare, isn’t it? So, you wish there were a CloudFormation feature preventing this from happening.
Luckily, CloudFormation has stack policies to help you in situations like this. In this post, I will talk about stack policies and how to use them as a supplementary protection mechanism in your stack updates.
Continue reading the AWS CloudFormation Stack Policy Conditions: Don't Replace or Delete My DB Instances on Stack Updates blog post.