Amazon S3 Storage Classes & Lifecycle Management: Optimizing Your Cloud Object Storage
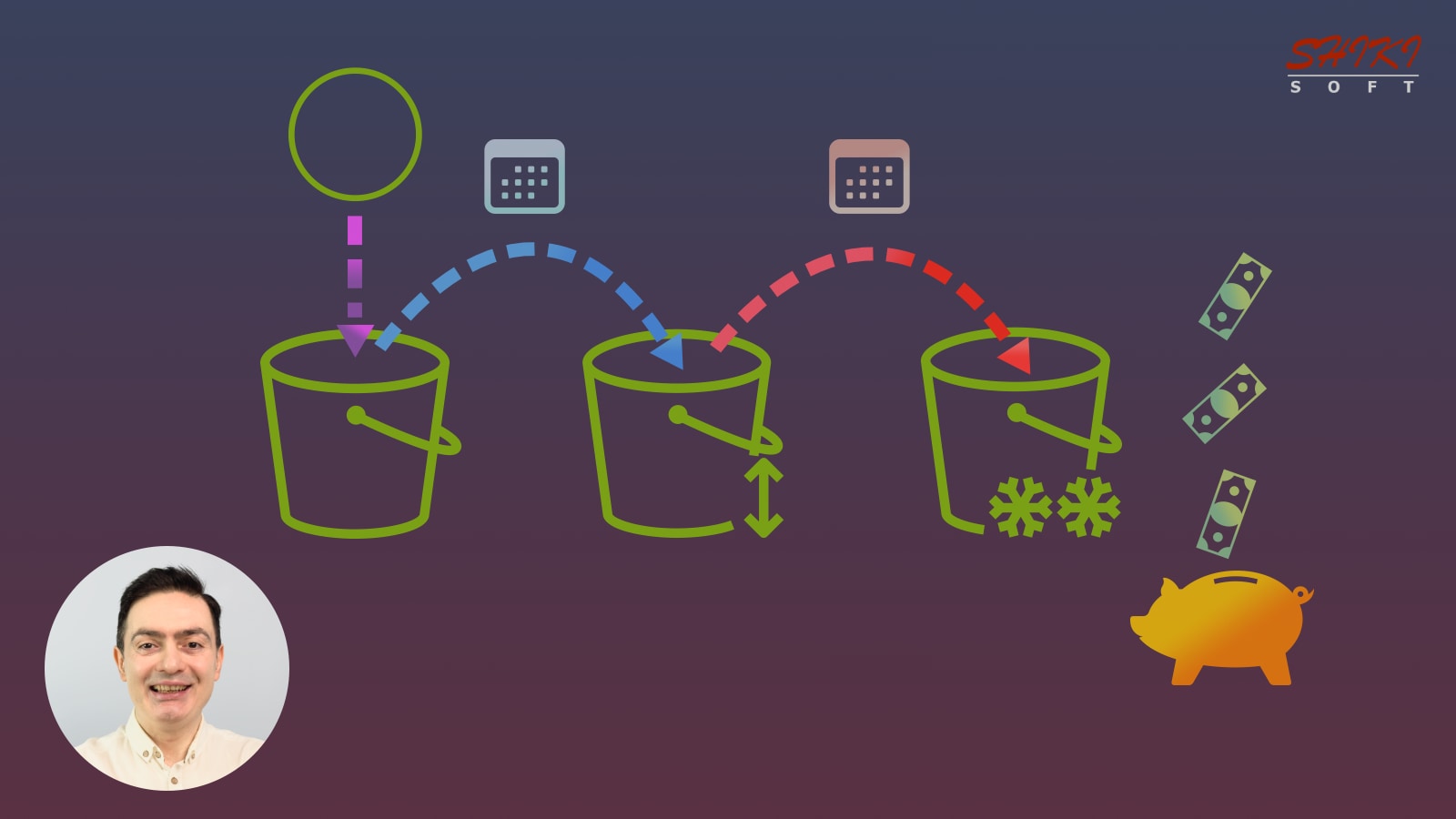
As a popular object storage service, Amazon S3 allows you to store data in buckets. However, in most cases, some data becomes irrelevant and less frequently accessed over time. If you leave things as they are, the data will continue to take up space, leading to extra storage costs, not to mention performance inefficiencies.
The good news is that Amazon S3 provides various storage classes for different access patterns that align with your storage performance and cost requirements. Besides, by configuring S3 lifecycle policies, you can transition objects to other storage classes or permanently delete them after a specific period.
This post will guide you through AWS S3 storage classes and introduce lifecycle policies to help you develop a cost-optimized and effective data management process.
Continue reading the Amazon S3 Storage Classes & Lifecycle Management: Optimizing Your Cloud Object Storage blog post.