Copying S3 Bucket Objects to Another AWS Account
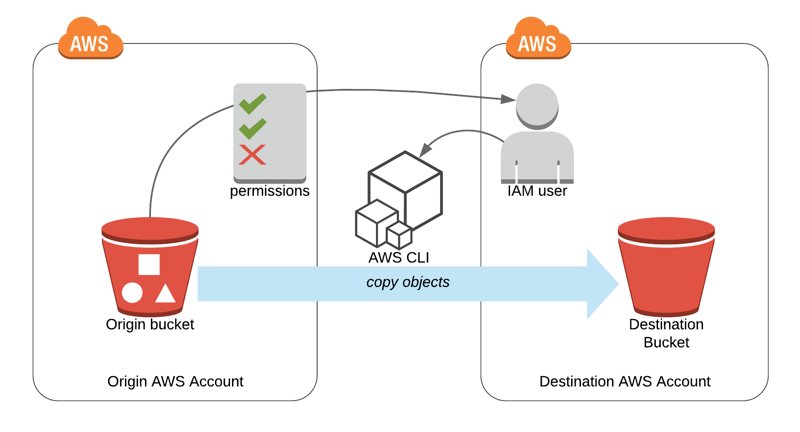
In some cases, you may need to transfer your objects in one of your Amazon S3 buckets to a different AWS account. AWS CLI provides high-level commands on S3 to move objects between two buckets. By also using Amazon S3 bucket policies, you can perform this even if the destination bucket is in another AWS account. Today, I will talk about the steps you need to do along with a few explanation on bucket and object level permissions.
Continue reading the Copying S3 Bucket Objects to Another AWS Account blog post.