A Quick Overview of IAM Permission Policies: AWS-Managed, Customer-Managed, and Inline Policies
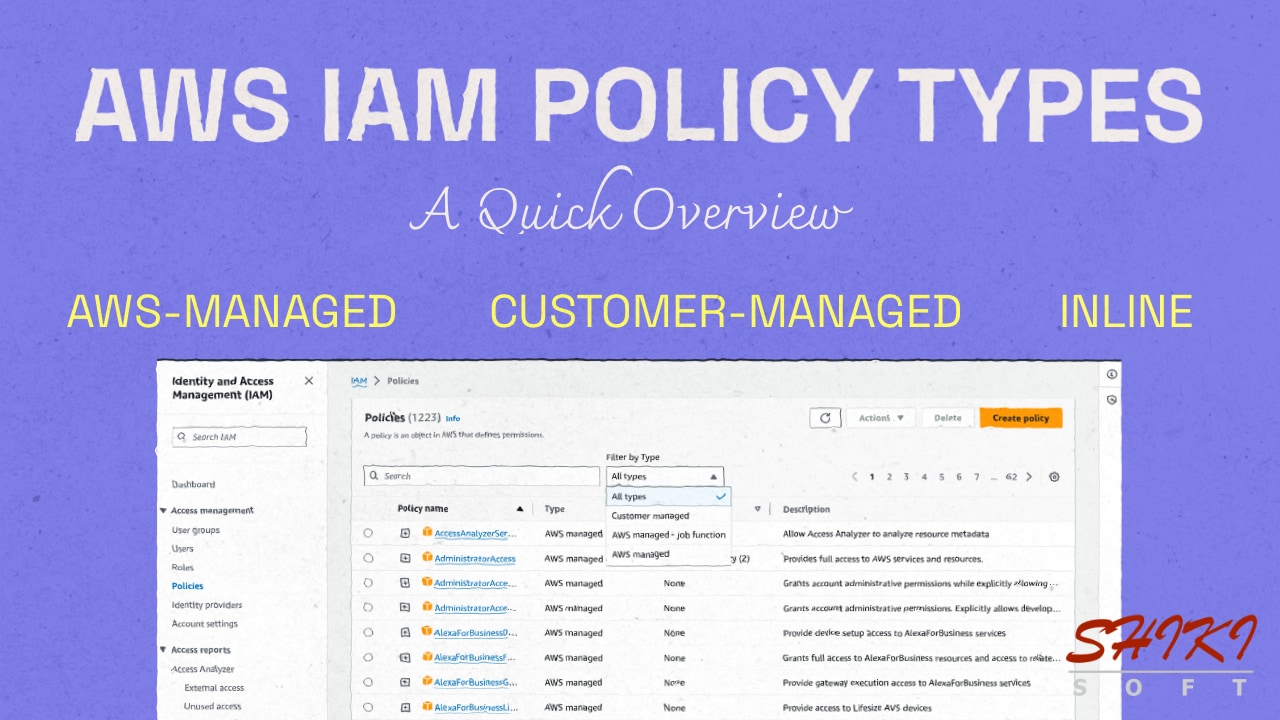
In AWS IAM, permission policies play a crucial role in securely controlling access to your AWS environment. You can attach three types of permission policies to your identities: AWS-managed, customer-managed, and inline policies. In most cases, AWS recommends using managed policies over inline policies, especially customer-managed policies created from AWS-managed policies. However, there may also be cases for inline policies. In this post, we will quickly explore IAM’s permission policies to help you decide which is best for you.
By the way, we will only talk about AWS IAM’s identity-based permission policies in this post. The resource-based trust policies used in IAM roles, in which you specify the principals you trust to assume a role, will be out of the scope of this post. So, when we use the ‘policy’ term below, it will only refer to an IAM permission policy: AWS-managed, customer-managed, or inline. Then, let’s begin.
So, when you attach a policy to an identity (a user, group of users, and a role), that policy determines whether to allow or deny access to your AWS resources. Hence, with security threats in mind, choosing the right policy type for your needs is essential, as well as granting the least privilege. But you wouldn’t want to increase the management overhead while doing this, right?
Each IAM policy type has its use cases. So, let’s analyze each one to see what features it offers.
Continue reading the A Quick Overview of IAM Permission Policies: AWS-Managed, Customer-Managed, and Inline Policies blog post.