In this blog, I talk about the benefits of defining your infrastructure as code using AWS CloudFormation from time to time. You define the properties of your AWS resources in a template and create a stack from it. When you need an update, you edit your template accordingly and update your stack. Don’t need a resource anymore? Just remove it from your template and update your stack again. Or, delete your stack if you no longer wish to keep any of its resources. In an ideal scenario, you keep your infrastructure code, your CloudFormation templates, in the same repository as your project and use a CI/CD pipeline to deploy it.
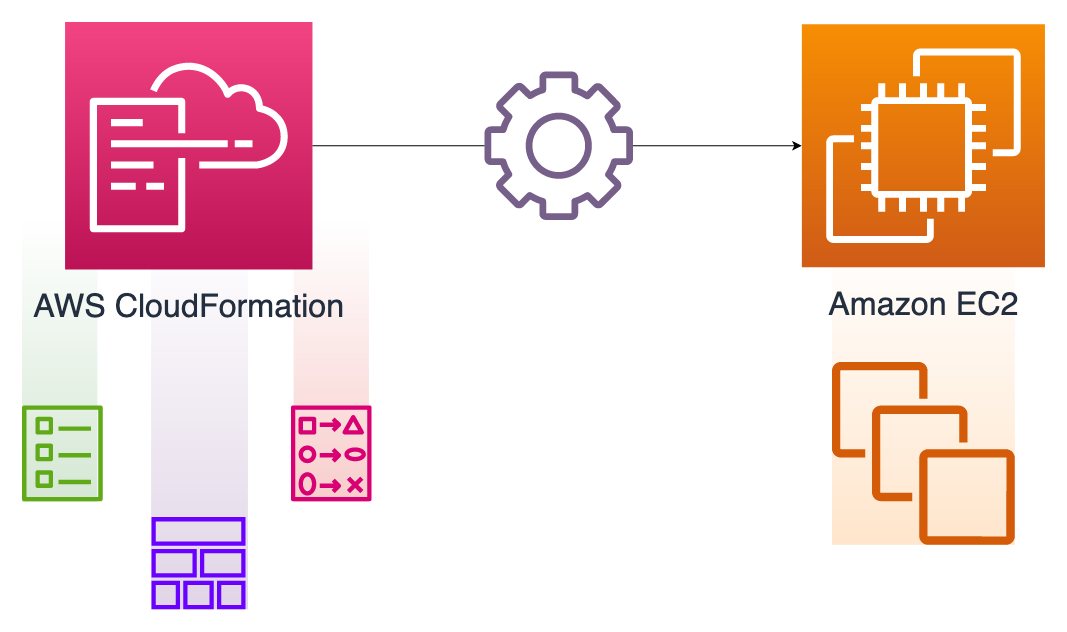
You can manage most AWS resources with AWS CloudFormation like this. However, Amazon EC2 instances are somewhat different. Again, you have properties like the subnet, instance type, or security groups of an EC2 instance as in other resource types. But, you also make custom, OS-level changes after creation, such as installing software packages, downloading or configuring files, etc. Besides, you may need to update this configuration later. It is why configuring an EC2 instance with CloudFormation needs more attention, and we have a dedicated section about it in my AWS CloudFormation Step by Step: Intermediate to Advanced course.
In this post, I will summarize how to manage EC2 instances using AWS CloudFormation. Firstly, we will discuss the UserData property. Then, we will continue with AWS CloudFormation helper scripts: cfn-signal, cfn-init and cfn-hup. We will also see the CreationPolicy attribute along the way. So, let’s start!
Continue reading the Configuring Amazon EC2 Instances With AWS CloudFormation blog post.