Orchestrating AWS Lambda Functions Using AWS Step Functions
- by Emre Yilmaz
- Jan 17, 2018
- AWS • Serverless • AWS Lambda • AWS Step Functions
While our serverless applications grow day by day; the need to orchestrate our Lambda functions may become an issue. We might need to execute some functions sequentially and one of our functions might get output of another function as input. Similarly, some functions might require to be executed in parallel. In these cases, AWS Step Functions can help us to coordinate our Lambda executions as components of our distributed applications and microservices.
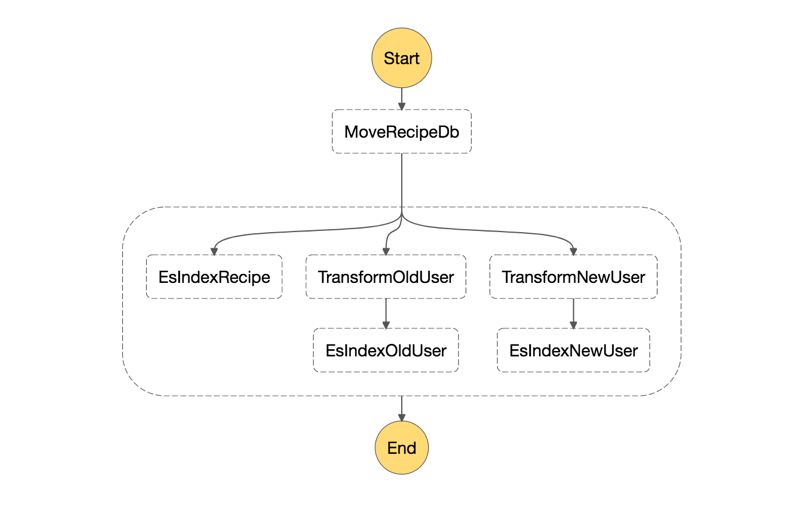
In this blog post, I will make an introduction to AWS Step functions with a simple case. I will try to show how we can define sequential and parallel executions, as well as intermediary states to transform one state’s output to pass another state as input.
Continue reading the Orchestrating AWS Lambda Functions Using AWS Step Functions blog post.